-or-
New tools to stop common laptop data thefts
Why your OPSEC advice is wrong
The internet security and privacy communities, law enforcement realms, all sides of the drug war, and the world as a whole have been enraptured by the unfolding saga of the Silk Road, the tor-hidden giant marketplace of illicit goods, and Ross Ulbricht, who stands accused of being its founder and leader, a.k.a. DPR, the Dread Pirate Roberts. A few months ago, he was arrested by the FBI in a library in San Francisco. It was only during court testimony in the past few days, however, that we learned the details.
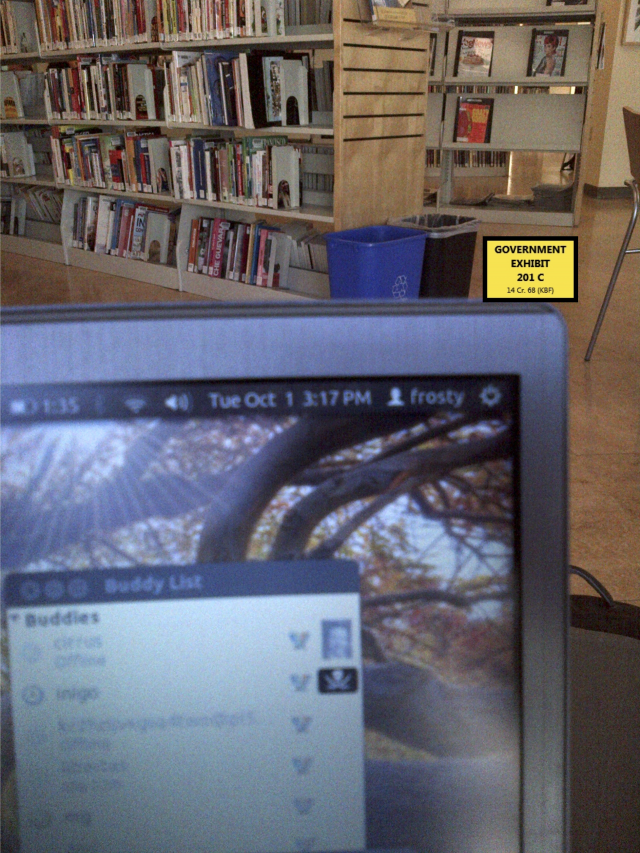
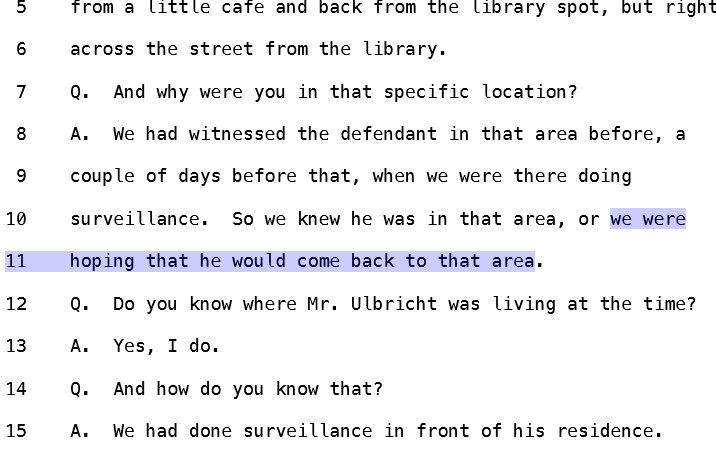
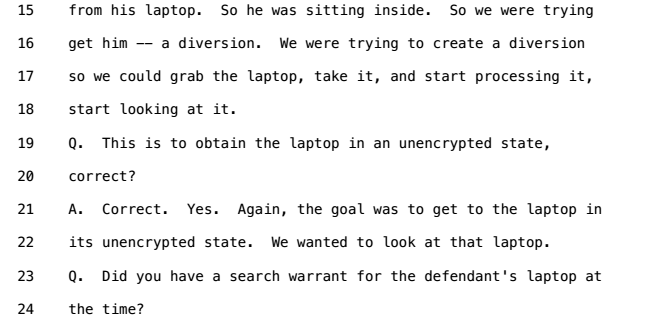
Having found Ross Ulbricht through his OPSEC failures early on in the establishment of the Silk Road, (he had recommended it on a Google-indexed forum under a screenname that also listed his name/email address, and he had written about a project of his that resembled the Silk Road) FBI agents were able to swoop in on him as he managed the silk road at a public library, and arrest him. The trial transcripts show how it went down; a male and female agent caused a diversion by yelling at each other "like a domestic dispute" right behind Ross. When he turned to look, they snatched his laptop and passed it off to their technical expert on site.
Despite early failures, he had been following current OPSEC advice. The grugq, in his popular OPSEC for Hackers, commands "Don't operate from your own house" as rule #5 to avoid law enforcement. The Intercept, the widely popular news outlet focused on leaked secret information, also insists "Go to a public WiFi network" in How to Leak to the Intercept, their advice to would-be leakers at risk of government prosecution. But in reality, the trial transcripts show this is just what the FBI wanted.
Despite putting Ulbricht's residence under surveillance, they waited until they knew he would be in public. Not only do the transcripts show that they wanted Ulbricht in a public place, but they also explain why.
Grabbing the running laptop let them obtain all the data that Ross was working on while it was still open and unencrypted, and let them see that he was logged in to the Silk Road as the administrator. The investigator copied off the contents of the documents folder to a USB drive he brought along.
The laptop was a treasure trove of information, holding mountains of incriminating evidence on Ross, from his private PGP key cryptographically tying him to the Dread Pirate Roberts online persona to his chat logs and notes detailing his operation. Ross's defense might have had a chance casting doubt on the prosecution if the FBI had not been able to obtain his unencrypted, running laptop.
So why does the Grugq and other say to not operate from home? "OPSEC for hackers" uses the example of Jeremy Hammond. While law enforcement were already staking out his Chicago residence, they were able to see an Apple computer active, which Hammond has admitted to using from one of his aliases, and it was active on TOR, which Hammond had also admitted to using online under an alias. In reality, LE had already identified him and his address from his online confession to having been detained at the Republican National Convention and other identifying comments. It was Hammond's big mouth that let LE find him, and it wouldn't have mattered if he had been using a library or coffee shop, once he was under physical surveillance, LE would have seen the same activity.
WinTheftProtection
Seizing a running laptop is a lot easier when its owner is in a public place like a coffee shop or library, but it can still happen in otherwise controlled environments, such as when the SWAT team busts in your door to seize your electronics and arrest you. This is why Taylor Hornby wrote SWATd, which will run a script when certain events happen, such as unmounting encrypted volumes when your Wi-Fi connection moves out of range (if your laptop was taken from your home, for example).
The big problems with this of course are that simply running a service called SWATd is effectively declaring you are attempting to obstruct justice and destroy evidence, which could easily get you in more trouble instead of less, and most users do not run a Linux operating system as their primary OS.
This is why I wrote WinTheftProtection which you can find at https://github.com/scriptjunkie/WinTheftProtection/ in source and binary form. If you want to use it, simply drop this file into your startup folder (C:\Users\yourusername\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup) and run it. By default, it will lock your screen when the power cord gets unplugged or plugged in, and if your network connectivity changes while the screen is locked, it will hibernate your system.
If someone snatches your laptop, even if you aren't able to grab the laptop, it's hard to imagine that you would not be able to grab or kick the power cord away, if the snatch didn't unplug it in the first place, and WinTheftProtection will lock it, shutting it down if it is moved too far away. So I recommend always using your laptop while plugged in to rely on WinTheftProtection.
It's important to note that the biggest remaining weakness is in tools like Inception that can use "FireWire, Thunderbolt, ExpressCard, PC Card and any other PCI/PCIe interfaces" to unlock your laptop with direct memory access. If you have one of those, even a locked screen can be bypassed; your best defense against that attack is to use a laptop without any of those interfaces. Update thanks to Jonathan Ketchum, Microsoft has documented how Windows can stop this attack by disabling Firewire/Thunderbolt via GPO and other OS's can as well.
Even if those attacks are stopped, a cold boot attack may still work, although it requires access to the computer memory with special tools immediately after poweroff. Automatically powering off your laptop will reduce the time period a thief has to apply those attacks, but nothing is completely foolproof.
Bottom Line
- Use Full Disk Encryption. It doesn't matter if you lock or shut down your computer if the data is sitting there unencrypted. Even if you encrypt a single document or a few files, accessing those files leaves forensic evidence all over your disks, logs, registry, and filesystem. Stick with either full disk encryption or use TAILS or another bootable CD that does not touch your hard disks at all, and use fully encrypted thumb drives to store your data.
- If your encryption choice uses a password, which most require, use a securely randomly generated one, not one you choose yourself and definitely don't re-use it anywhere else.
- Don't access your sensitive information in an uncontrolled environment, like most coffee shops or public libraries.
- Use something like WinTheftProtection as a last ditch line of protection against the snatch.
*Of course I don't actually support organized crime, 99.9% of snatched laptops are ordinary thefts, not FBI stings. Because of that, I think it's unlikely that this article will even help criminals get away. But be honest, you'd much rather read "How to run a secret drug empire and hide your incriminating evidence" than "Boring article about laptop thefts."
Just in case you get the wrong ideas, let me be clear. Don't be a drug lord, hire contract killers, or run hacking rampages across the web. Even with these tools and this advice, it's too easy to make a mistake like Ross or Jeremy did for any of that stuff to be worth it. Save it for protecting your information from common thefts or legitimate whistleblowing, and check out Colorado or support decriminalization efforts if you don't like the drug war.