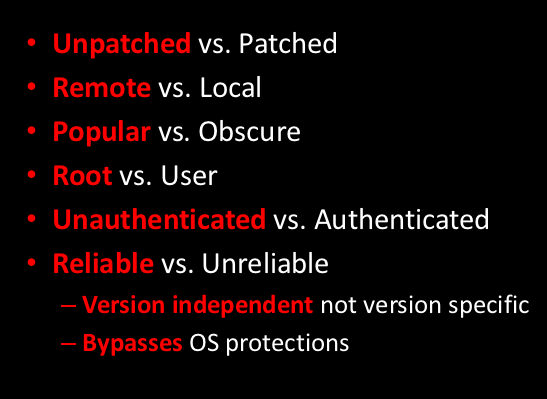
You can see the slides I put together for my talk Network Nightmare - Intel PXE at http://www.scriptjunkie.us/wp-content/uploads/2011/10/Network-Nightmare-Intel.pdf. It is a modification of the Defcon talk, and adds some lessons learned/suggestions for developers. I also added a few slides evaluating the PXE attack according to the most common vulnerability severity criteria, as if it was a vulnerability instead of insecurity by design:
Network Nightmare (Intel)
Comments are closed.
#1 by Chris John Riley on December 18, 2011 - 6:16 pm
Great work on the PXE stuff… was wondering if you’d thought about using it to perform social engineering for things like full disk encryption. PXE boot the target and prompt for the FDE password etc…
Keep up the good work.
Chris
#2 by scriptjunkie on December 18, 2011 - 11:46 pm
Thanks Chris! I thought about that but have not implemented it that far. I don’t have a way to write to a Bitlocker disk from Linux even if I did have the credentials (I assume Bitlocker is most popular) and other ideas took precedence. But if you have/know somebody who has code to do this, feel free to send it my way.
If I can fit in the time to complete it with the other projects I am working on, the next thing I am working on is developing a similar attack for UEFI, and/or AMT.
The feedback I got from Intel after this talk was basically “Yes, PXE is terrible; have you looked at the new stuff?” So since then, I did a little research, (and I just got hardware that supports those) and boy, AMT (http://j.mp/vaRhfS) has powers that make PXE cower in shame. So that’s the next logical step.