sessionthief
It's now 2013, which makes it over 6 years since sessionthief was written. Yahoo Mail and Facebook now offer SSL encryption, and GMail uses it by default, in large part due to the awareness that programs like sessionthief brought to the problem. That means that now sessionthief often does not work against the biggest targets, but there are still plenty of other websites out there that are vulnerable to hijacking.
sessionthief is a program to perform HTTP session cloning by cookie stealing. It can do some simple host discovery and can perform ARP Poison Routing to get packets if you are not connected to a hub or open wifi network.
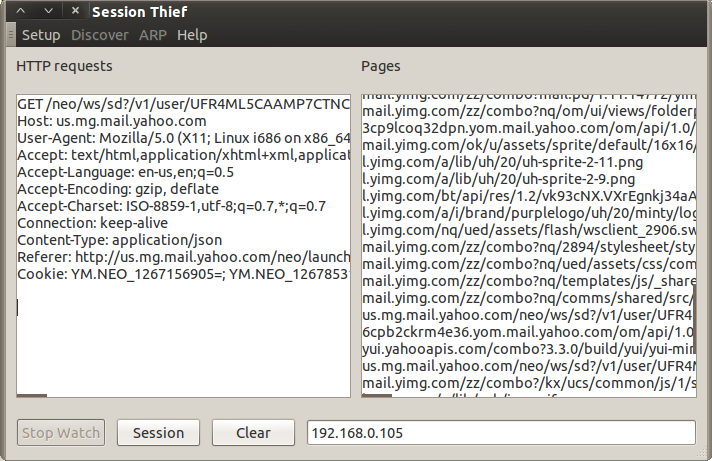
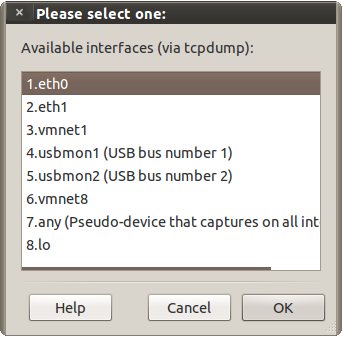
It integrates automatically with Firefox, dynamically creating a temporary profile for each attack performed. For example, if multiple clients on the open or WEP-encrypted wireless network you are on are on facebook (or yahoo mail or just about any site you log into), you can 1. start the program, 2. select your interface, 3. hit watch, and 4. select a request from each of them to facebook, and click the session button. The program will start a new instance of firefox for each session hacked, and let you control the login of all of them at once.
It compiles and runs on linux and windows depending on the pcap and wxwidgets libraries. The source and binaries for windows and linux are at https://github.com/scriptjunkie/sessionthief or in a downloadable zip: sessionthief.zip.
If you have a different Linux version or architecture, compile it yourself. First, install the development libraries for gtk2, wxwidgets, and libpcap:
# apt-get install build-essential libwxgtk2.8-dev libgtk2.0-dev libpcap-dev
Then unzip the sessionthief folder in some directory and cd into the sessionthief folder. The complete compilation can be performed in one command:
$ g++ $(wx-config --cppflags --libs) -lpcap -o sessionthief *.cpp
Ideally, you should give it the raw net capability and run it normally:
setcap cap_net_raw,cap_net_admin=eip sessionthief
Otherwise, you will need to run as root or have tcpdump installed setuid root (run # chmod 4755 `which tcpdump` as root) to get packets live or you can open a pcap file saved from tcpdump or wireshark, etc.
Sessionthief also now includes an automatic update feature; it will display a message on startup when it detects a new version.
#1 by genuix on April 25, 2013 - 9:20 am
Hi sir,
Congrat for you so great work, realy apreciate it.
I tryed to compile it in the new Kali system i just installed.
Just to tell you about a possible typo in 2 files of the sessionthiefSRC:
nviewFrame.h:44:27: fatal error: processthread.h: No such file or directory
processThread.cpp:3:27: fatal error: processthread.h: No such file or directory
in both case i just correct the “t” to “T” in the included file name and is’t compiled well.
Cheers
Jeff
#2 by scriptjunkie on April 27, 2013 - 3:50 am
Thanks for the bug report! Should be fixed now.
#3 by resetter on October 16, 2013 - 4:53 pm
Hey,
compiled sessionthief on kali, but i get the following errors on running it:
http://pastebin.com/KwsguW6G
#4 by scriptjunkie on October 18, 2013 - 3:23 am
Hi resetter, looks like I have an old version up there. Try downloading the zip file and compiling again. I don’t have Kali, but I made some changes to make it work on the system I am on now.
#5 by resetter on October 18, 2013 - 3:32 pm
Thanks for your efforts but I now get errors while compiling, I have all the dependencies installed.
Compile errors:
http://pastebin.com/NkS9bU0i
#6 by scriptjunkie on October 20, 2013 - 2:03 am
Seems to be a different version of WxWidgets than I have. Try again! I went ahead and put it onto github so you can see the development if you want. https://github.com/scriptjunkie/sessionthief/commit/47600e7a4b75969b25b52d130c75eac65719968e