You'll be happy when they can't spy on you.
? ? ???? ? ? ? ? ?
Schadnfreude is a new end-to-end encrypted, anonymous ID and IP-hiding, decentralized, audio/video/file sharing/offline messaging multi-device platform built for both communications and application security and performance.
What does all that mean?
Well what if you didn't just hope your messages weren't being read by employees of big tech firms or spy agencies (like Gmail, Teams, Skype, or Facebook Messenger)?
What if you didn't want Google or Apple to know exactly who was receiving messages you send, even if they don't see the contents (like Signal, Telegram, WhatsApp, Wire, Threema, and more that all use push notifications)?
What if you wanted to collaborate and synchronize data, files, folders, even git repositories and not just hope a single server or host could get compromised and go down or reveal all the data from all the projects (GitHub, Slack, Discord, and as has recently happened to thousands of GitLab servers)?
What if you didn't want to have your entire messaging system collapse when one organization or even one engineer made a change (like has recently happened to Signal, WhatsApp, and many of the rest)?
What if you didn't want to give Google, Microsoft, Apple, or others the ability to push malicious updates to your communications software that will steal your private messages when you know these have complied with invasive information gathering orders in the past?
What if you wanted to protest abusive policies and not reveal your real identity and location to everyone you talk to and anyone who swipes one of their unlocked phones, which can be a matter of life and death in some places (Signal, WhatsApp, Telegram, all phone-number-based apps)?
What if you wanted a higher level of assurance your messaging program wasn't using technology known to be dangerously vulnerable to serious attacks like buffer overflows and privileged script injection that could compromise not just one conversation but every message you have ever sent or will ever send and every file on your computer (such remote code execution vulnerabilities that have been recently found in C/C++ and Electron code in WhatsApp, Signal, Teams, and others)?
Texas Cyber Summit (TCS) 2021 Slides
Schadnfreude debuted at the 2021 Texas Cyber Summit, in San Antonio, TX. Slides can be downloaded here: Beyond E2E PDF
Goal
Schadnfreude's goal is to provide all the advantages of a traditional secure messaging platform without the pitfalls of centrally-controlled services and vulnerable technologies. Specifically, it seeks to anonymize endpoints, hide IP addresses, prevent user enumeration, eliminate single points of failure, and categorically prevent the most common and severe vulnerability classes, while preserving the performance, convenience, and features of other secure messaging applications.
Implementation
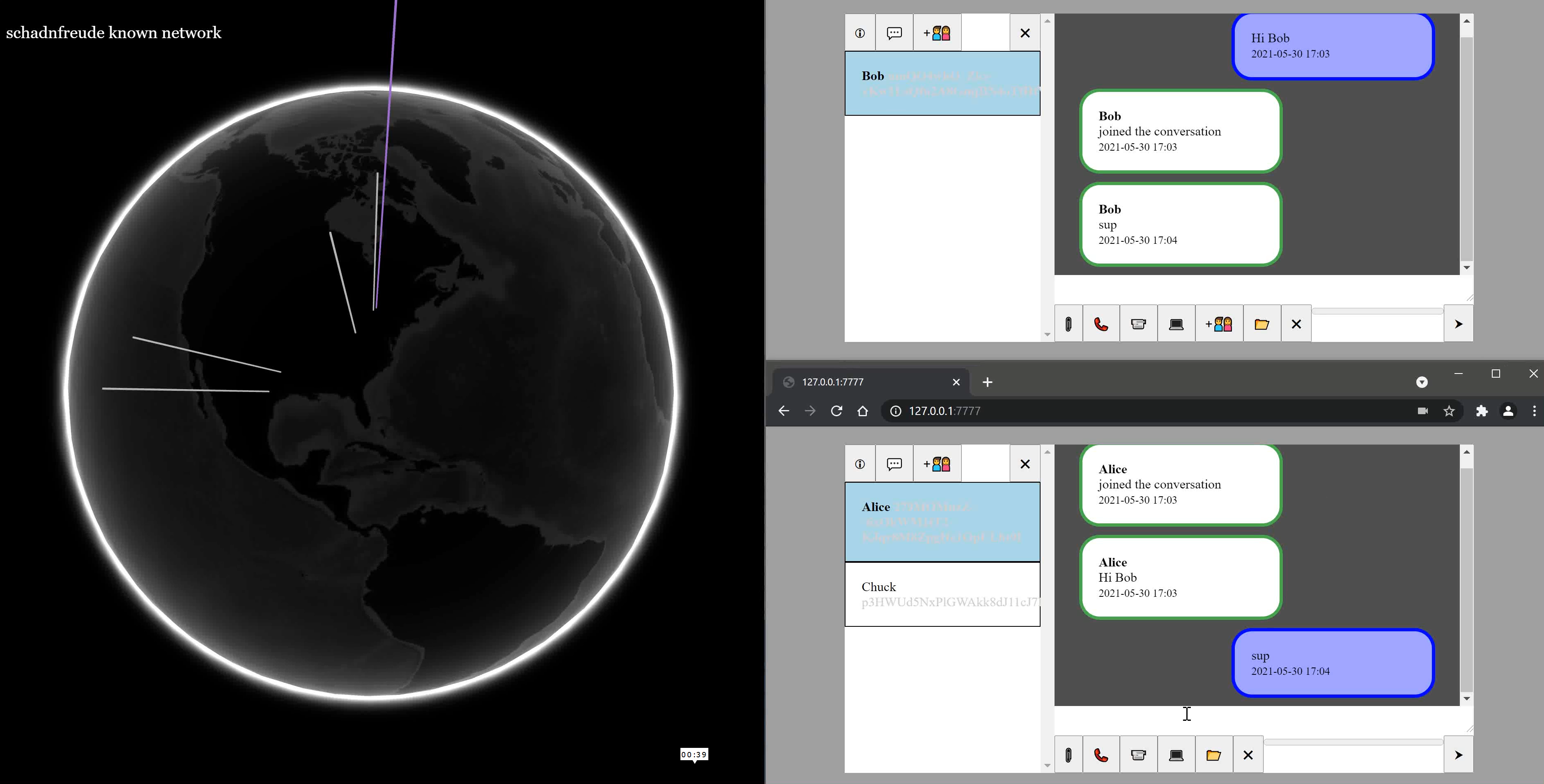
Schadnfreude uses a network of nodes to perform its anonymizing functionality. The schadnfreude client selects one or more meet nodes to use long-term, but may change it later if desired. The meet node holds offline encrypted messages and files, but cannot read them or see who is accessing them. The schadnfreude client never connects directly to its meet node, instead setting up tunnels through one or more relay nodes first. Likewise, relays are used to connect to other clients' meet nodes as well.
Schadnfreude uses a message-based model riding over UDP by default for maximum performance and security. This allows it to reduce round trip times combining cryptographic and traditional connection initiation, and better support realtime audio/video communications, allowing packet drops. Connection metadata is authenticated, which allows us to better resist man-on-the-side attackers seeking to cause a denial of service among other threats.
Contacts are identified by public key. Such keys are used when setting up a conversation, which establishes a symmetric key to authenticate and encrypt messages between two endpoints. This key may be shared later with additional contacts to invite them to the conversation and enable them to see the group messages.
Comparison
Other applications like Signal, WhatsApp, and Telegram are only built to protect message contents from third parties. They each use a centrally-controlled set of servers that can see the metadata (who sends and receives messages, when, and how big they are) as well as even the contact lists of their users. Such information includes real phone numbers and IP addresses of users, which are tied strongly to their real-world identities, making such messengers a very bad choice for users who need to conceal their identities while communicating.
Much of this information, such as IP addresses, is visible to not only the central servers but also the cloud providers they run on, the ISP's they use, and since those mobile messengers use Google Cloud Messaging and Apple Push Notification Service to notify your phones, metadata about messages including the real recipient identity is also visible to Google and Apple. In each of those apps, by default the user's IP address is also directly revealed to anyone they voice or video call. Even if one of those entities promises not to retain this information, nothing prevents the others from doing so, or the first from being compelled to at some point in the future.
Metadata exposes enormous amounts of sensitive personal information everyone should be concerned about revealing. In Why Metadata Matters the EFF illustrated how metadata provides enough context to know some of the most intimate details of your lives.
In addition, the users are at the mercy of a centrally-controlled server and application ecosystem and are vulnerable to service disruption from many sources.
Not so with Schadnfreude.
Schadnfreude's relaying hides IP addresses, meet nodes avoid single point of failure and tracking, and public key based chats and key derivations avoid identity tracking, even by the meet nodes. This also prevents user/endpoint enumeration and spamming that has happened in earlier anonymity networks or phone number-based secure chat systems.
License
schadnfreude is licensed under both the Apache2 and MIT licenses. Unlike other messaging services, this includes both client and server code.
Comparison
Prawned (last post) is a very quick proof of concept of a few techniques, focused on a very difficult threat model, and as a result it has few functions, just sending text, which is not immediately delivered. Schadnfreude is a much larger project that has been in the works for longer and allows immediate and high-volume communications, such as video, audio, files, and more.
Release information
Schadnfreude is now released at https://gitlab.com/schadnfreude/schadnfreude/ Linux and Windows binaries are found in the 0.2.0 release. Linux binaries can also be found in the CI/CD artifacts. It can be manually built for Windows or as a library for an Android app. As this is a very early release, it should be treated as a proof-of-concept. It has not been audited, and the default configuration is not hardened.
A node server can be started by running schadnfreude -n and a client can be started by running the executable without parameters.
What now?
Try it out and give feedback (issues on the gitlab server please).
The network is very small now, so run a node and help out.
If you're the kind to look at code, do that, and maybe even contribute.
Demand more of your communications and collaboration software.